CIA World Factbook 2022-2023 | Book by Central Intelligence Agency | Official Publisher Page | Simon & Schuster

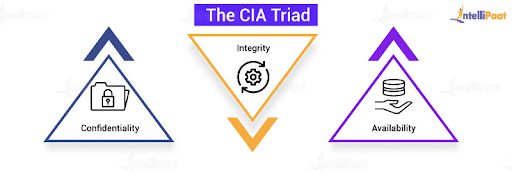
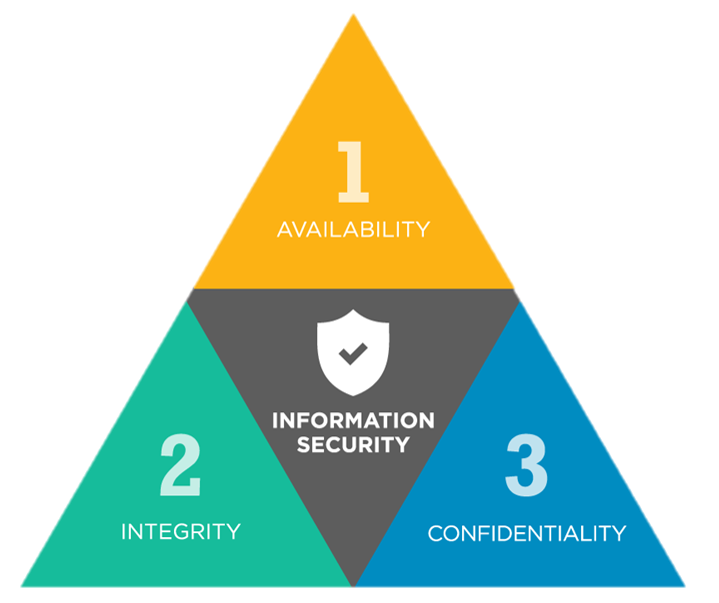
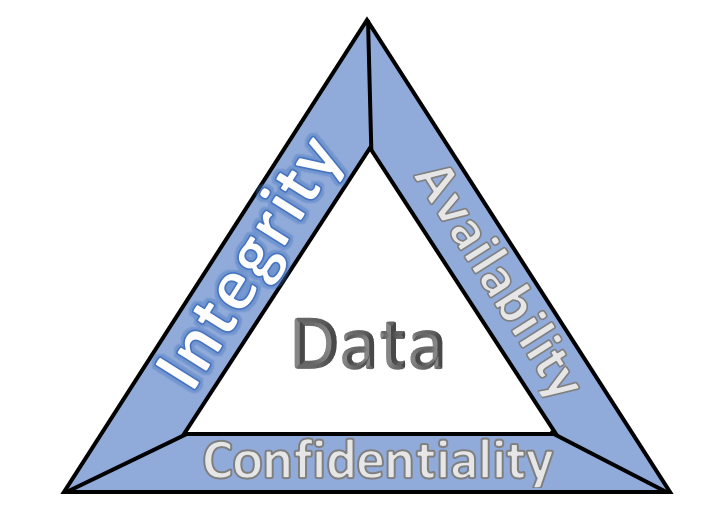
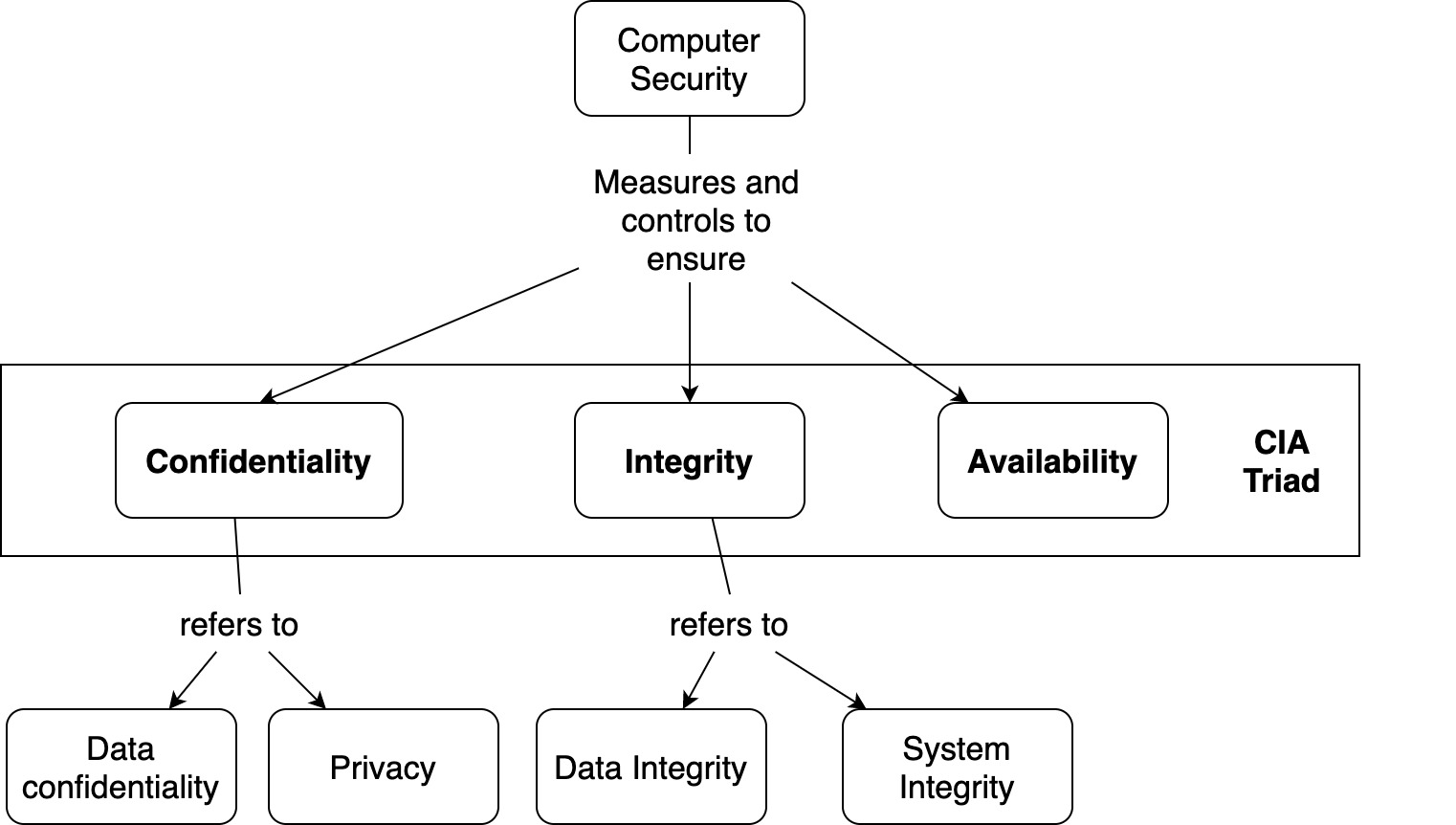
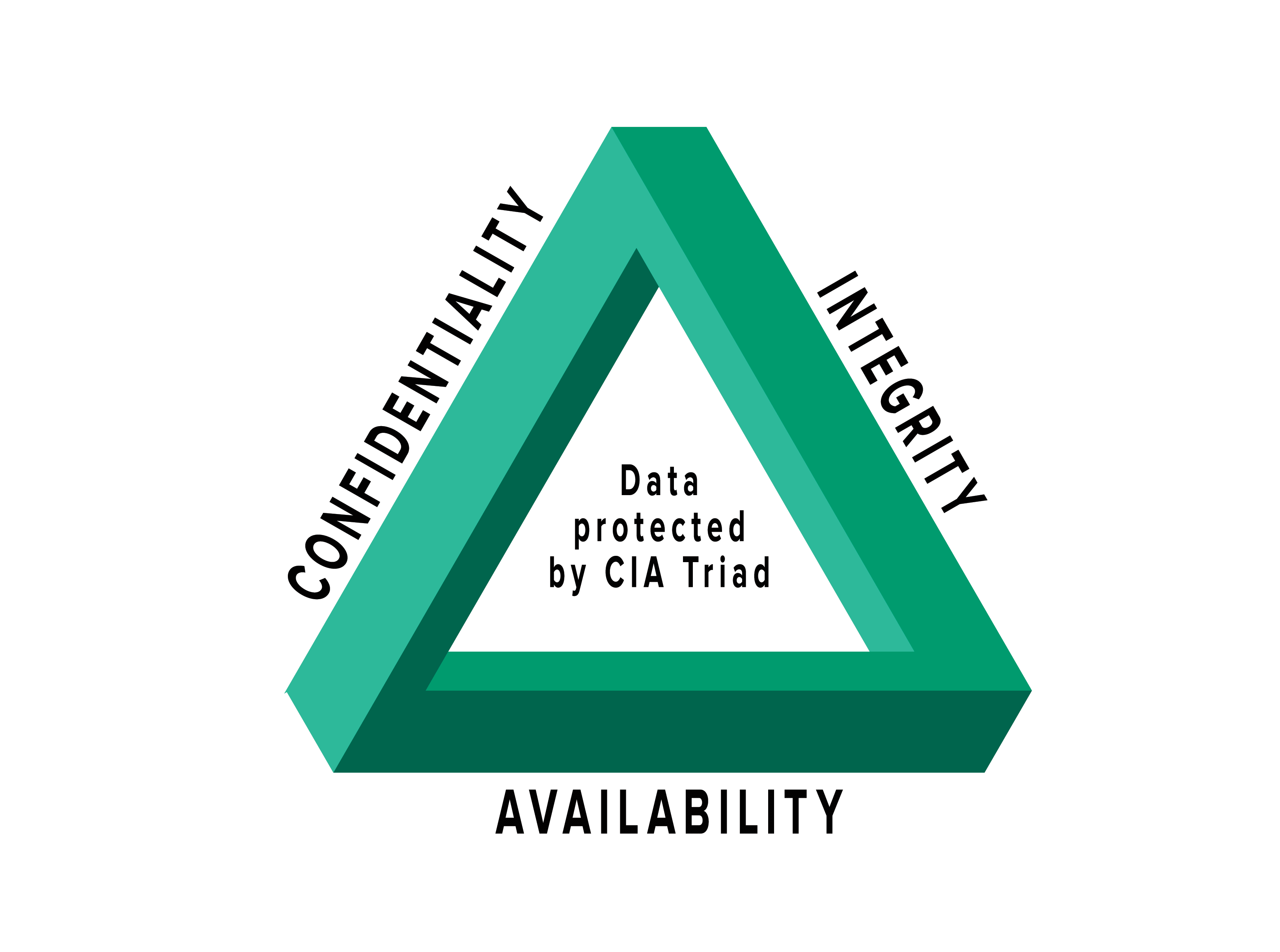
CyberShelter - The CIA Triad Three basic information security concepts important to information are Confidentiality, Integrity, and Availability. If we relate these concepts with the people who use that information, then it

Confidentiality Integrity Availability Stock Illustrations – 34 Confidentiality Integrity Availability Stock Illustrations, Vectors & Clipart - Dreamstime
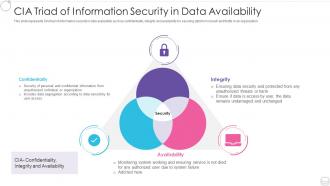
Cia Triad Of Information Security In Data Availability | Presentation Graphics | Presentation PowerPoint Example | Slide Templates