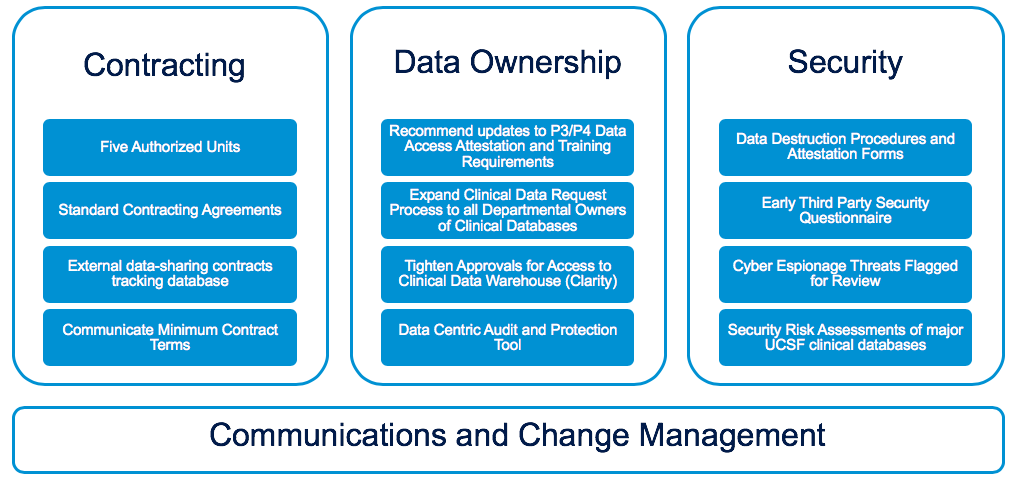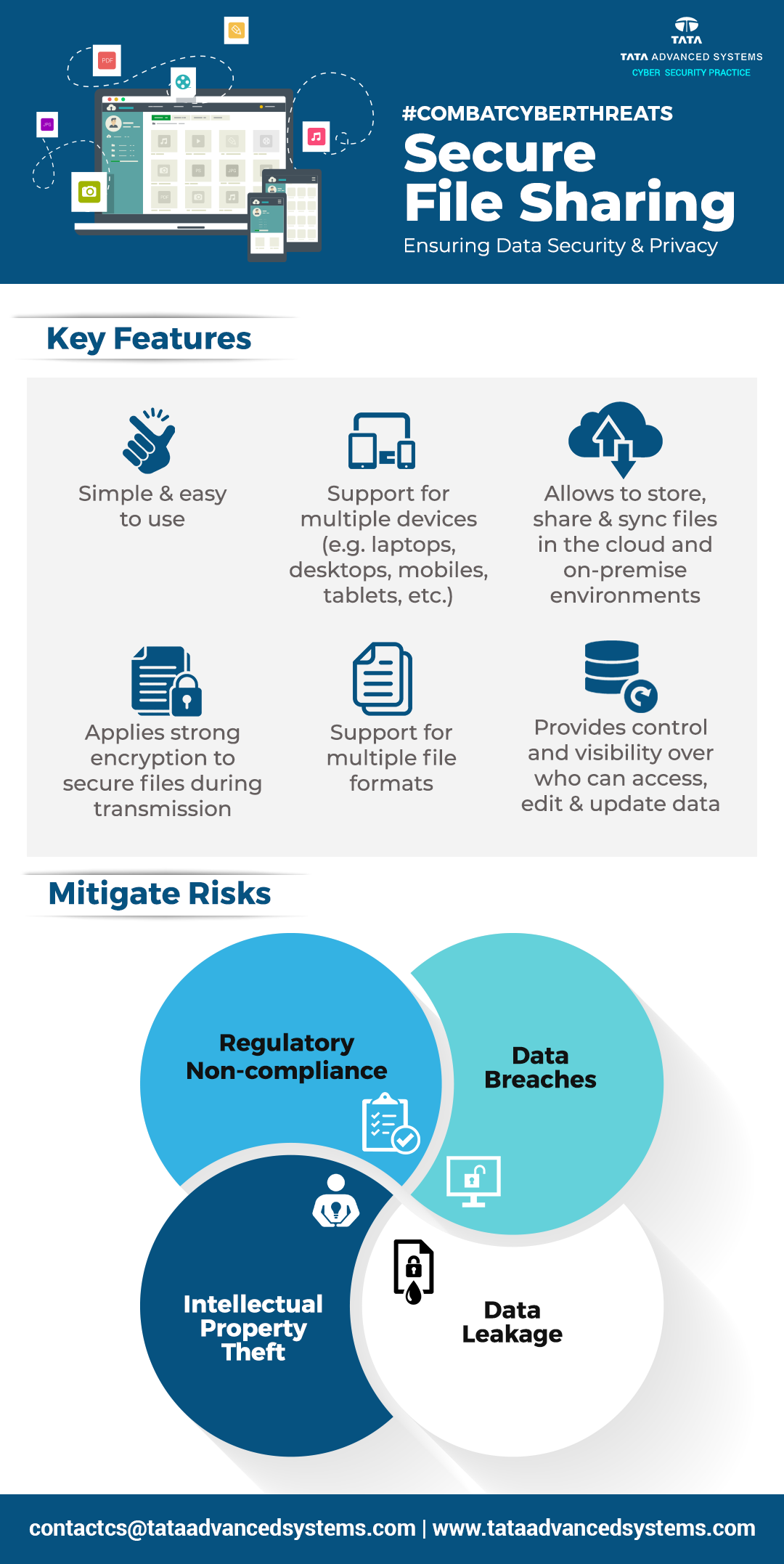
Secure File Sharing- Ensuring Data Security and and Privacy | NASSCOM Community | The Official Community of Indian IT Industry
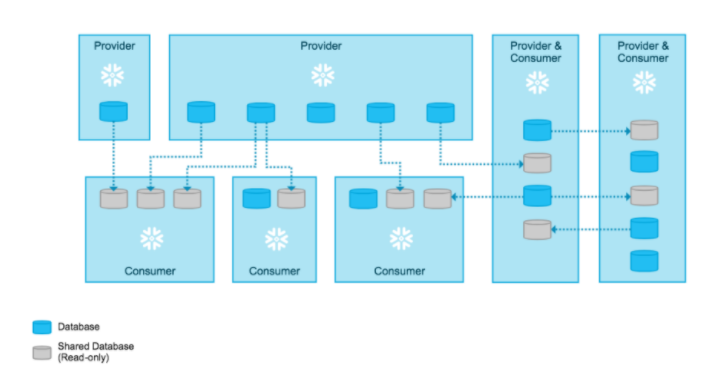
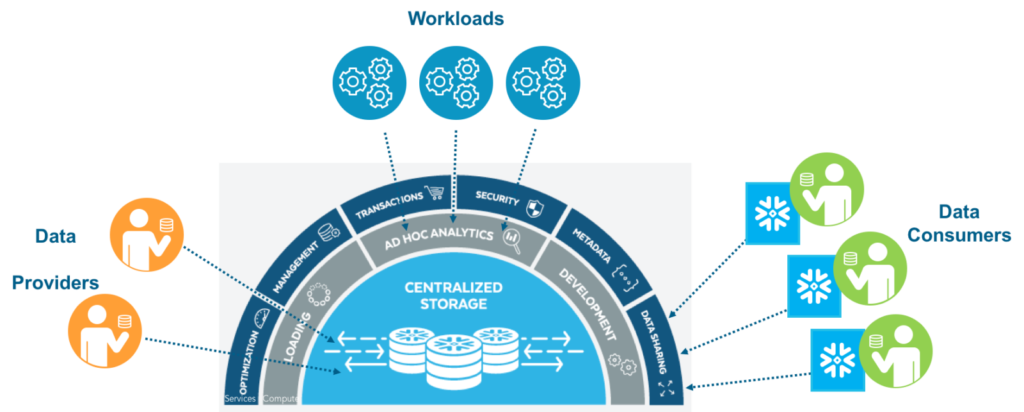
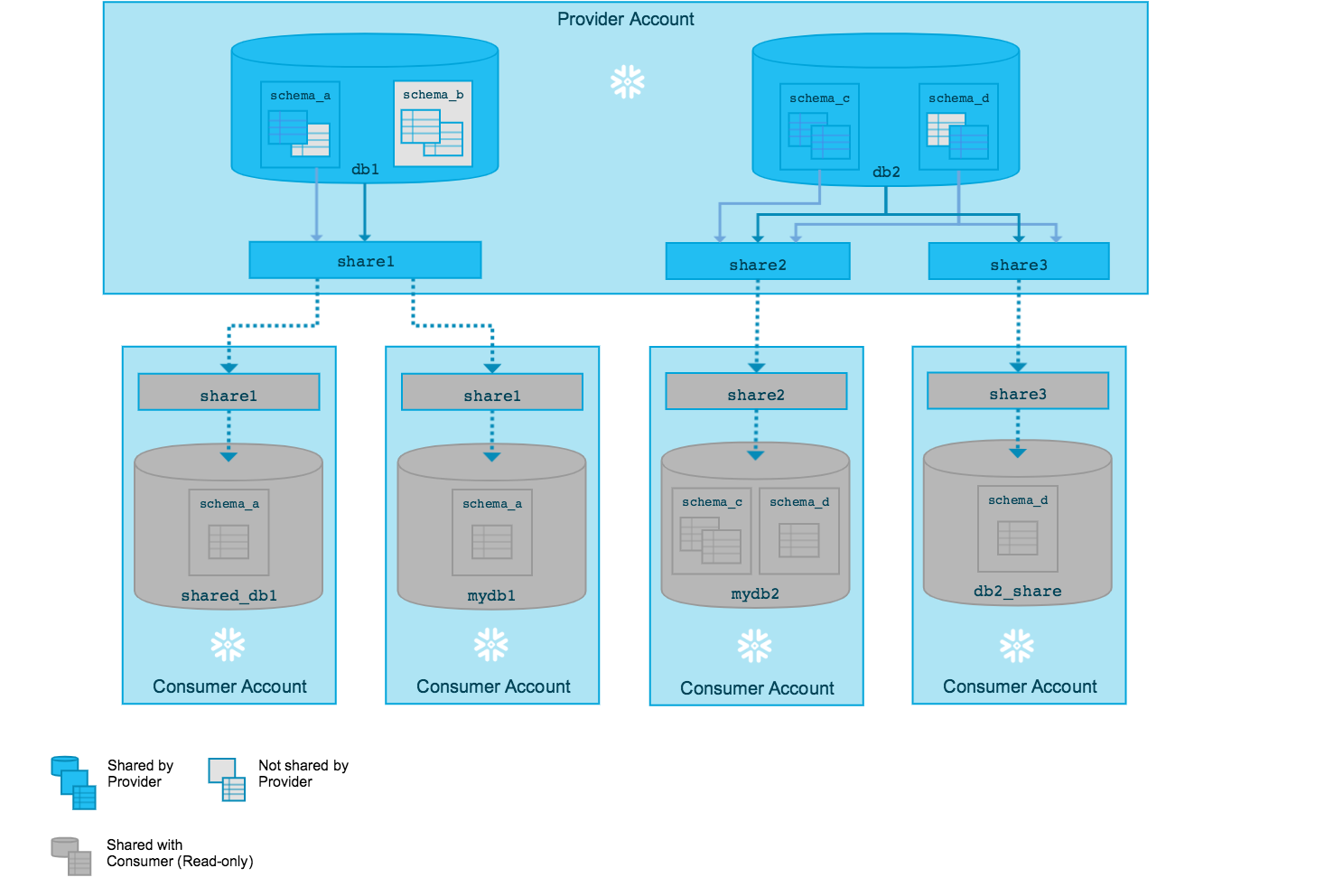
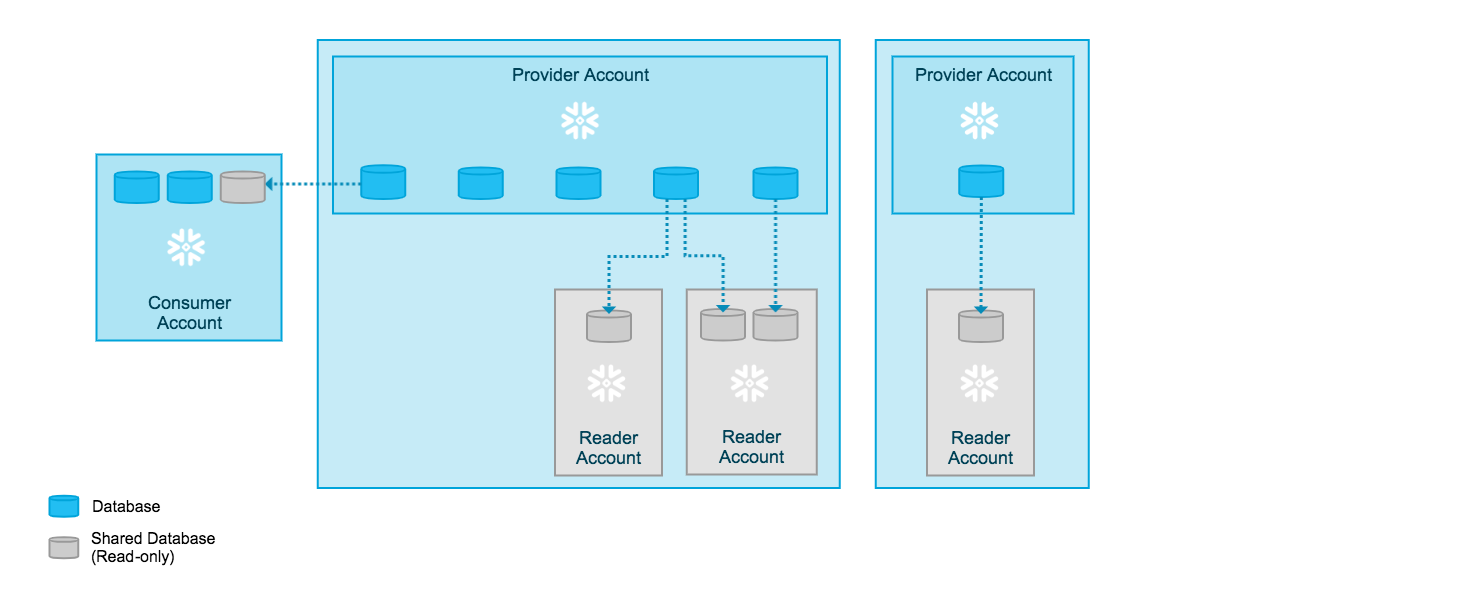
Secure Data Sharing SnowFlake. 1. Architecture & Key Concepts | by Diwakar | Beer&Diapers.ai | Medium

Are Data Rooms Secure Enough to Share Your Sensitive Data? Here is the truth - Locklizard Document Security Blog
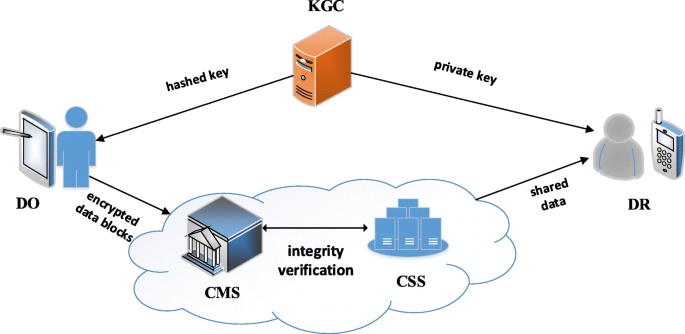
![PDF] Secure Data Sharing in Cloud Computing Using Revocable-Storage Identity-Based Encryption | Semantic Scholar PDF] Secure Data Sharing in Cloud Computing Using Revocable-Storage Identity-Based Encryption | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5c58aac4966433014cd2bdf3ac593e6f16b1c635/2-Figure1-1.png)
PDF] Secure Data Sharing in Cloud Computing Using Revocable-Storage Identity-Based Encryption | Semantic Scholar